Despite its name, Open Banking does not make financial information widely accessible to anyone. Accessing banking information is only possible in controlled and secure environments due to issues relating to value, confidentiality and risk. For a party to retrieve financial data, it has to be authorised, identify itself to the data holders, and have the permissions of the data owners. In this article, we will only focus on Authorisation and Identification.
Authorisation and Identification
Understanding the difference between Authorisation and Identification is crucial to comprehend why there are risks involved with only checking the eIDAS certificates. Authorisation relates to the TPP’s (Third Party Provider) permissions and rights—i.e., what it can do. Identification is the key to proving a player requesting access is who they actually claim to be. So, how can a TPP be authorised, and how are they identified?
Authorisation
A narrow definition of a TPP is that it is a payment or electronic money institution that can provide payment initiation and / or account information services. Therefore, an entity that plans to become a TPP needs to:
- Get a PI / EMI license
- Gain permission to provide services 7 and 8 of the PSD2
- Request passporting rights if it plans to act outside of its Home Country
The diagram below demonstrates how a TPP becomes authorised. They firstly apply to their national supervisory entity, known as a National Competent Authority (NCA). After being granted permission to carry out payment services, the TPP may be apply for passporting also through their home NCA, who in turn asks NCA of the country where they want to provide services. This process culminates in the publication of the TPP’s Unique Identifier, the services that it can provide, and its passporting rights in their Home National Register.
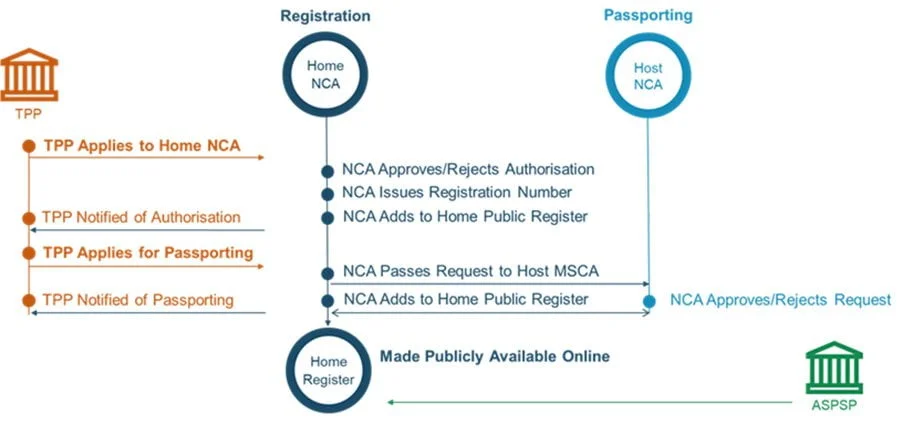
Identification
Once it is authorised, a TPP can start to onboard ASPSPs (Account Servicing Service Providers), but it has to prove its identity. According to article 34 of the EBA Regulatory Technical Standards on strong customer authentication and secure communication under PSD2 (RTS SCA/CSC), a TPP as to identify itself with an eIDAS Qualified Certificates (Qwac or QSeal).
Qualified Certificates are aimed at enhancing trust in electronic transactions across the EU and are regulated through the eIDAS regulation. eIDAS defines requirements on Qualified Certificates; and the Qualified Trusted Service Providers (QTSPs) that issue these certificates ensure their trustworthiness. QTSPs are supervised by a National Supervisory Body to assure that these requirements are met. The ‘Qualified’ status makes the certificate legal and trustworthy, indicating it meets specific technical and security requirements.
Article 34 of the RTS SCA/CSC for PSD2 defines that PSD2 Qualified certificates must have additional content requirements, namely:
- The Authorisation Number issued by the National Competent Authority (NCA)
- The role(s) of the PSP
- The name of the NCA where the PSP is registered
Why checking certificates is not enough
Although PSD2 Qualified Certificates are a trustworthy method of validating the TPP’s identity, they cannot be used to attest its authorisations because:
- eIDAS certificates are designed for identification (not authorisation)
- There is no mechanism to ensure that the certificate is updated if the source of information (i.e., NCA register) changes.
- The eIDAS certificate does not carry PSD2 passporting information.
As a result, relying on Qualified Certificates to validate a TPP authorisations can lead to improper access being granted. This mainly happens when the passporting rights do not match those in the certificate or when the TPP loses its permissions.
Passporting Rights Mismatch
Thanks to the freedom of establishment and the provision of services (commonly known as passporting), TPPs based in the EEA do not have to be limited to their Home Country. However, to act abroad, they have to be authorised. Therefore, having the right to access accounts in the Home Country is not a confirmation that a TPP also has access to accounts throughout the EEA. There are two possible cases of a passporting mismatch, either the TPP has no passporting rights, or it has passporting rights that do not contemplate services 7 and 8 of the PSD2.
In both cases, the outcome is the same—the TPP has the possibility of obtaining a valid PSD2 Qualified Certificate. An ASPSP that only relies on Certificates to confirm the authorisations is incurring the risk of granting access to entities that are not allowed to act in their market. As of June 2021, OBE estimates that, on average, one in four TPPs passported into any given country in the EEA has information on its eIDAS that differs from the information on its passporting rights.
TPP Loses its Permissions
If the status of the PSP changes and any authorisations are revoked, the QTSP will not revoke the certificate unless it is informed of the change by the NCA or the PSP itself.
It is, therefore, possible for certificates to remain valid even if the authorisations are no longer valid, given that the identity authenticated through the certificate is still correct.
The NCA is not obliged to inform the QTSP, and the QTSP is not obliged to check the NCA register.
If an NCA has withdrawn a license and the certificate has not yet been revoked, there is a period when the roles in the certificate will not be accurate. Should any party wish to check the up-to-date role of a PSP, they must look at the Home NCA of that entity.
How to Check Access
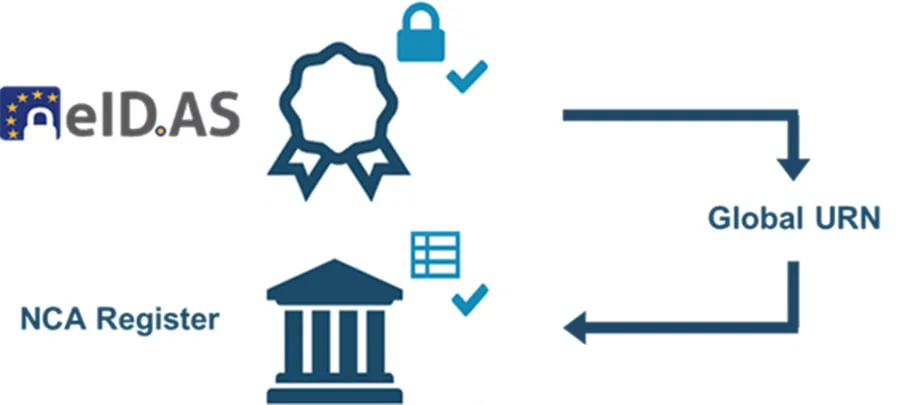
ASPSPs must rely on the eIDAS certificates to validate the Identity of TPPs; however, to verify the Authorisations, ASPSPs should check National Registers, provided by the local supervisory body..
The National Registers are a requirement of PSD2 (Article 14), and they contain all the information needed to validate the TPP’s Authorisations.
As a warning, ASPSPs should not rely only on their National Register to validate authorisations, especially for entities from foreign member states but they need to check the NCA register of the TPP. As a TPP can come from any country, this involves being able to check all the registers in Europe.
Difficulties in finding and interpreting 31 national registers mean that most banks use a commercial service which consolidates and standardises these sources of information.

John Broxis
Managing Director, Open Banking Exchange
This content was originally published in July 2022 by Open Banking Exchange. Open Banking Exchange advisory and consultancy services are now being provided by Konsentus. This content is therefore now available to visitors to the Konsentus website.





